VLANs revisited
Introduction
Back in 2001, I did a web page on VLANs, you can still see this via the index. But since then, technology has moved on, Layer 3 switching is now commomplace, and edge switches are increasingly being used as a form of network security. So I reckoned it was time to revisit VLANs. Much of this web page is the same as the last one, but it also contains some new information.
One of the features of many switches is the provision of VLAN`s, or Virtual Networks - a VLAN is a method of splitting up a physical network into a number of logical network segments.
The result is that computers or hosts attached to one VLAN can only "see" the other computers or hosts in the same VLAN, and not those in other VLAN`s. More precisely, broadcast messages such as ARP requests are only transmitted within the confines of the VLAN.
VLANs operate at layer 2 of the OSI model.
What VLAN`s look like
A switch providing say 3 VLAN`s would, at the physical level, look like any other switch, ie,
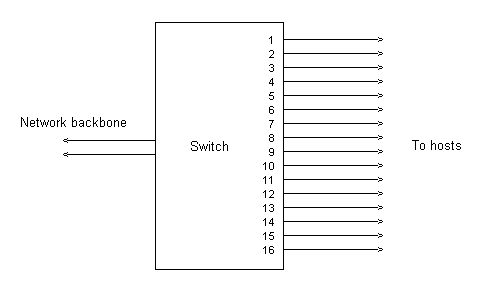
However at the logical level, it would look like
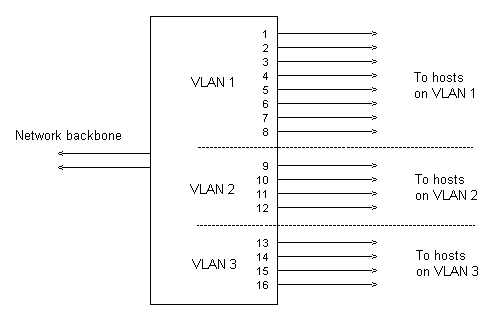
The 3 sections defined as VLANs are functionally separate at the layer 2 level.
Data traffic between hosts connected to ports in the same VLAN is just as normal. The switch sets up a temporary exclusive connection between the two ports which lasts only as long as the transmission time of the data packet, and no other port, and hence no other hosts, see the data packet.
Now it is of course the primary function of switches to provide virtual connections between two hosts, so that data flow between these two hosts is isolated from all other hosts.
However a considerable percentage of data traffic on any network segment is broadcast traffic, ie, a host sends out some form of data without a recipient address, and it is the duty of a switch to distribute this across the whole network segment.
For a switch operating without VLANs being set up, this would mean that every port on the switch would see the broadcast trafic, and pass it on the hosts connected to the ports.
However, because the switch now has functionally separate sections, the VLAN`s contain this broadcast traffic, so that it is only sent to hosts within the respective VLAN, hosts on other VLANs don`t see it.
So now broadcast traffic within VLAN 1 will only be distributed to ports 1 - 8, ports in the other VLAN`s will not see it.
Likewise, broadcast traffic within VLAN 2 and VLAN 3 will only be distributed to the ports within these respective VLAN`s.
The setting up of VLAN`s has therefore created what some texts refer to as "broadcast domains".
Some effects of VLANs
It is important to note that the splitting up into VLAN`s is done by specifying to which VLAN each switch port is assigned.
The host does not neccessarily know it is part of a VLAN - the assignment is done through the switch port.
This has two effects -
If a host is moved from one part of the physical network segment to another part, it may end up being connected to a port in a different VLAN - so the switch will have to be reprogrammed. This will cause a substantial workload if the site has several VLAN`s and a lot of end user workstations.
Instead of connecting a host such as a computer onto a switch port, a hub can be connected, and then all the ports on the hub are on the same VLAN as the switch port.
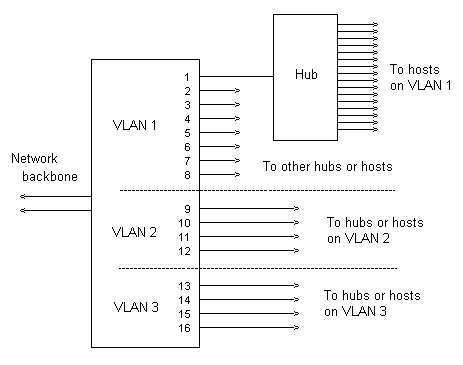
However it is unlikely that this would be done in modern networks.
Extending VLANs
The use of hubs is one way of increasing the size of a VLAN, but is really only suitable where all the hosts are in the same physical location, eg, on one floor of an office block, or in one medium sized building on a campus which has several separate buildings.
If it is required to extend a VLAN so that it includes hosts that are dispersed in different parts of the site, then other methods are required.
The first method which can be used is to connect switches together through one port in each switch, and set up these ports all to be in the same VLAN.
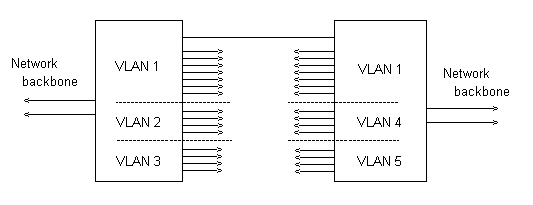
The drawing shows that in each switch, port 1 has been assigned to VLAN 1.
However this is not realy a recommended method -
it uses up ports on each switch, and if there are several switches which have to be connected together in this way, then another pair of ports is used up for each additional switch
there has to be installed a separate cable for each pair of switches that have to be linked in this way - if there is considerable geographical separation between the switches, then this can be a real problem
Again, it is unlikely to be done in a modern network.
A much better solution is to use the already installed network backbone to transmit information about VLAN`s to all the switches in the network. This is done using a protocol that all the switches understand.
Early protocols were mostly manufacturer specific, and were not always understood by switches from other manufacturers. For example,
3Com developed VLT ( virtual LAN trunk )
Cisco developed ISL ( inter-switch link ) for use on fast-ethernet, and 802.10 for use on FDDI
Later, the IEEE developed the standard known as IEEE 802.1Q as an open protocol for defining VLANs.
It`s basic method of working is to add a section to the header of the MAC frame. This section is known as a tag.
This extended frame can then be transmitted like any other frame over the network backbone, and the receiving switch extracts the tag, and hence the VLAN information.
It is essential that both the sending switch and the receiving switch are set up to understand tagged frames. If a tagged frame is sent to a device that does not understand tagging, it will see the extra section in the header as wrong information, and the frame will be dropped.
Currently, IEEE 802.1Q is widely used, but some manufacturers such as Extreme have equipment that understands both IEEE 802.1Q and Cisco ISL.
The IEEE 802.1Q tags
The tag used in IEEE 802.1Q is a frame extension that is inserted into the MAC frame after the destination and source addresses. It consists of 4 bytes of information, which includes an identifier, and a 12 bit VLAN number. The 12 bits used for the VLAN number allow for 4096 different VLANs within a network. However VLAN numbers 0 and 4095 are reserved, so in practice, there are 4094 available VLAN numbers.
VLANs and subnets
The use of VLANs divides up a large network into smaller funtional pieces, which is fine for limiting the traffic generated by broadcast messages. However it causes problems when hosts on one VLAN need to interact with hosts on other VLANs. The conventional approach to this was to use some form of routing to connect VLANs.
However the growth in the use of layer 3 switches has resulted in a slicker way of doing this. Most modern layer 3 switches are dual band - they function as layer 3 switches and as layer 2 switches.
Usually the layer 2 switching is done by ASIC`s at a hardware level, and the layer 3 switching is done in software.
To use this facility within a layer 3 switch, each VLAN is married to its own subnet IP network address.
So traffic within a VLAN is handled by the ASIC based layer 2 part of the switch. And traffic between VLAN`s has now become traffic between subnets, and so the software driven layer 3 component is used for this.
VLANs and security
If VLANs are being used for the purpose of achieving a high degree of isolation between parts of a network, then the use of layer 3 switches may not be the best approach.
To maximise the isolation of VLANs from a security point of view, layer 2 only switches would be used for the traffic within the VLAN, and an 802.1Q aware firewall is used as a router to pass or block traffic between VLANs.
Downside of VLAN tagging
There is a downside to VLAN tagging - the addition of the 4 bytes of tagging has extended the length of a frame by 4 bytes. So if a frame has been constructed with the maximum length of 1518 bytes, and an IEEE 802.1Q tag is added to it, the frame now has an illegal length of 1522 bytes. Any network node that is not 802.1Q tagging aware will drop this frame.
Also, even if the frame is below the legal maximum length, the 802.1Q tag means that the frame is constructed in a way that will not be understood by network nodes that are not 802.1Q aware, and again, the frame will be dropped.
So it is essential that 802.1Q tags are removed by the edge switch, before the frame is sent out to the computers.
Other types of VLAN
It is worth saying that 802.1Q tagging is not the only way to define VLANs. They can also be defined by other mechanisms, such as
configuring the switch ports to pass or block particular types of layer 3 protocols
mapping MAC addresses to VLAN membership
directly configuring switch ports
© 2006 Ron Turner
Return to the index page