Using Red Hat Linux 9 as a network firewall
Introduction to this webpage
This page describes a possible way to use Red Hat Linux 9 as a firewall. It is based on the use of iptables, which is packaged with Red Hat Linux 9.
This page is about using a Red Hat Linux 9 box to protect a secure subnet behind the firewall, and is based on the restriction that the Linux box is not used for any other purpose - that means no other purpose - the GUI is not used, no server functions, nothing. All control is done from the command line, using a shell script for convenience.
Personal viewpoint
The protection provided by a firewall is only as good as the protection which is given to the firewall itself against cracking by attackers via the internet.
By also using the Linux firewall box as any kind of server means that you are opening up your Linux box to attacks through the ports that have to be opened to allow the Linux box to function as a server.
I therefore strongly recommend that the Linux box which is running as the firewall is used for no other purpose.
Initial setup of the Linux box - 1
If you have installed Red Hat Linux 9 as an upgrade from a previous version of Red Hat Linux, then it is very probable that your linux box has on it an earlier firewall technology called "Ipchains".
Ipchains must be removed from your linux box before you can use iptables - iptables will detect if ipchains is on the linux box, and will not run.
If you install Red Hat Linux 9 as a new installation, then the default is to use iptables.
On the basis of my personal viewpoint expressed above, I don`t see any justification for doing an upgrade from a previous version of Red Hat Linux - wipe the box, and start with a new installation.
When you do the new install, select the minimum installation option, and during the setup configuration, accept the option to install the firewall ( referred to as Lokkit ).
It doesn`t really matter which of the firewall options you select, you are going to remove their settings anyway. However by installing the standard firewall, it means that the Linux installation has the various bits and pieces of iptables already installed.
Initial setup of the Linux box - 2
Even if you do the mininum installation, Red Hat Linux 9 is still rather fat - it is still over 470 Mb`s of stuff, much of which you don`t need, and some of which you definitely don`t want on a network firewall. Especially Sendmail.
Even in the minimum installation, Sendmail is not only installed by default, it also runs by default in run level 3. So at the command prompt enter
service sendmail stop
It is then neccessary to stop Sendmail running when the Linux box is restarted, so you can use Setup for this. However it is preferable to remove Sendmail all together from the System V initialisation sequence, so at the command prompt enter
chkconfig --del sendmail
Whilst you are at it, it might be worthwhile getting rid of stuff like isdn, pcmcia, portmap, rhnsd, and sshd.
By default, in the minimum installation, these services are all started at boot-up. There is no point in wasting processing resources on services that are not required, and any service that is runnable is a source of weakness for attackers to exploit.
In addition, three other services, ie, irda, nfs, and saslauthd, don`t start by default at boot-up time in run level 3, however they do exist in the System V installation sequence, so it might be advisable to "chkconfig --del ....." them as well.
Introduction to iptables
The first thing to know about iptables is that it is not an application or a daemon.
Iptables itself is in essence a set of rules that the kernel uses to process packets of data that arrive via either of the network interfaces eth0 or eth1.
However having said that, there is an application associated with iptables, it is the application that interprets commands entered at the command prompt, or via a shell script, and turns these commands into a set of rules understood by the kernel.
The background to this firewall
This firewall is being used within the following network configuration :-
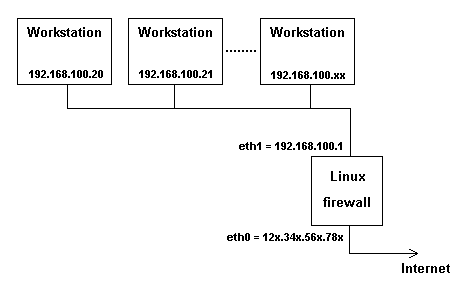
There are no servers on the 192.168.100.0 subnet.
DHCP is not being used.
The workstations are manually configured with their ip addresses within the 192.168.100.0 subnet, and with the default gateway in each workstation set to 192.168.100.1.
The Linux firewall has two network cards :-
eth1 is connected to the 192.168.100.0 subnet, and has the ip address of 192.168.100.1.
eth0 is connected to the outside world, and for this web page, has been given the mythical ip address of 12x.34x.56x.78x.
The protection given by the firewall as configured below is based on several features of the iptables system :-
Network address translation
Port blocking
IP address blocking
Packet filtering based on connection status
As mentioned above, the kernel part of iptables is "programmed" through the user interface also called iptables, which user interface is based on the command line environment.
So in theory it is possible to do the programming directly at the command prompt - however my preference is to use a shell script, which can be fully commented.
The shell script attached to this page is sufficiently commented that no other description or explanation should be required.
The shell script shown is a sanitised version of a working script, with several Microsoft Windows XP workstations hiding behind the firewall. You will of course have to modify it to suit your particular environment.
To use such a script, there are a number of ways to get it to run at boot-up time.
Modify the iptables initialisation script contained in /etc/rc.d/init.d/iptables by adding the rules to this script.
A fairly advanced level of scripting skills is required for this approach.
I have tried running the firewall script from a command line in the initialisation script - it runs fine, and loads the rule set as it should. However the firewall doesn`t work, this appears to be because ip forwarding through the firewall has not been enabled in the kernel, even though it is specified in the firewall shell script that it should be enabled. At present I don`t know why this should be.
Add a line to the end of the /etc/rc.d/rc.local initialisation file. For example,
sh /ipt/iptables-13
Much simpler to do, and I have found this to be quite a reliable way to run the firewall script at boot-up. However this method can suffer from the disadvantage that there is a short period of time during the boot-up period, after the iptables initialisation script has run, and before the shell script runs, when the linux box may be wide open to attack, as the rule set has not been applied.
Also simple to do, manually run the shell script -
sh /ipt/iptables-13
Then instruct iptables to save the resultant rule set as a configuration file stored in /etc/sysconfig/iptables - iptables should allow this to happen using the command
iptables-save
However in Red Hat Linux it doesn`t work properly - it saves the rule set to the file /etc/sysconfig/iptables, but during a reboot, the rule set does not get applied. At present I don`t know why.
Better results are obtained using the command
service iptables save
This saves the rule set to /etc/sysconfig/iptables as it should, and the rule set gets restored on boot-up.
This is simple to do, and avoids the "open window" period.
However for this firewall configuration, this method is not useable - whilst the rule set does get successfully restored, it is only the rule set that gets saved and restored. Any other types of command in the firewall script do not get saved and restored. So the command line in the script that says
echo 1 > /proc/sys/net/ipv4/ip_forward
is not saved and restored - and it is this line that sets up the ip forwarding, and without it, the FORWARD chain will not work.
So this method is not useable for this firewall configuration. There should not be a problem if your firewall application does not need the FORWARD chain.
Still to do
The production of this firewall script is not the end of the development to use Red Hat Linux 9 as a firewall - there are other things that can be done to improve perfomance.
Kernel modules - there are several kernel modules associated with iptables. There may be some that can contribute to the protection provided by the firewall, but which are not currently being utilised. There may also be some that are used by default, which would be better not used.
Recompiling the kernel - the kernel supplied with Red Hat Linux 9 has been compiled to provide a host of facilities that are not required in a firewall - there could be performance improvements obtained by slimming down the kernel.
There are some kinds of attacks which haven`t been covered yet, such as Denial of Service attacks and SYN flooding. So the rule set still needs some work done to it.
Finally ...
Here is the firewall script - version 13 - it is a bash shell script, not an html page, and was written using Vi. It should be possible to download it from here as a shell script through your browser. Some browsers actually manage to display it as a web page.
© 2004 Ron Turner
Return to the Firewall index page