Numbered extended access lists
Introduction to this web page
This page contains two sample numbered extended access lists. Numbered access lists were introduced in IOS version 8.3. This list uses "remark" as a way of adding comments to the list. "Remark" was introduced in IOS version 12.
This list isn`t really complete, as it doesn`t allow any routing protocol into either interface. It also doesn`t have any information about other configuration settings of the router.
It isn`t a script as such, because it also shows the relevant prompt. From these prompts, it can be seen that all the configuration of a numbered access list is done in Global configuration mode - unlike the situation with named access lists, in which the configuration of the access list is done from within a specific access list mode.
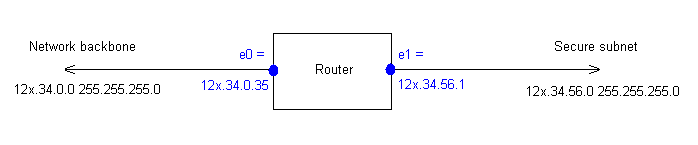
The list is based on the following network arrangement :-
The commands
router> enable router# config t ! router(config)# ! Remove the previous version of the access list ! router(config)# no access-list 110 ! ! ! router(config)# access-list 110 remark **This list is for incoming packets** ! ! router(config)# access-list 110 remark **This section blocks packets with source addresses router(config)# access-list 110 remark that should not exist on the open internet.** ! ! router(config)# access-list 110 remark **This is the loopback address** ! router(config)# access-list 110 deny ip 127.0.0.0 0.255.255.255 any ! ! router(config)# access-list 110 remark **This is sometimes used to mean "this" host** ! router(config)# access-list 110 deny ip 0.0.0.0 0.0.0.0 any ! ! router(config)# access-list 110 remark **These are the IP addresses reserved by IANA** ! router(config)# access-list 110 deny ip 10.0.0.0 0.255.255.255 any router(config)# access-list 110 deny ip 172.16.0.0. 0.15.255.255 any router(config)# access-list 110 deny ip 192.0.2.0 0.0.0.255 any router(config)# access-list 110 deny ip 192.168.0.0. 0.0.255.255 any router(config)# access-list 110 deny ip 240.0.0.0 7.255.255.255 any router(config)# access-list 110 deny ip 224.0.0.0 15.255.255.255 any ! ! router(config)# access-list 110 remark **This is our own secure subnet address** ! router(config)# access-list 110 deny ip 12x.34.56.0 0.0.0.255 any ! ! router(config)# access-list 110 remark **This is the network address of the network router(config)# access-list 110 remark backbone, and there are no hosts on this router(config)# access-list 110 remark backbone, only routers ** ! router(config)# access-list 110 deny tcp 12x.34.0.0 0.0.0.255 any router(config)# access-list 110 deny udp 12x.34.0.0 0.0.0.255 any ! ! router(config)# access-list 110 remark **This section allows incoming packets with router(config)# access-list 110 remark specific port numbers.** ! ! router(config)# access-list 110 remark **In addition, some entries will only allow router(config)# access-list 110 remark an incoming packet if it is part of an router(config)# access-list 110 remark established tcp connection - `ack` or `rst` router(config)# access-list 110 remark is set. This is a simple form of stateful router(config)# access-list 110 remark packet filtering.** ! ! router(config)# access-list 110 remark **Telnet** ! router(config)# access-list 110 permit tcp any eq 23 12x.34.56.0 0.0.0.255 established ! router(config)# access-list 110 remark **DNS** ! router(config)# access-list 110 permit tcp any eq 53 12x.34.56.0 0.0.0.255 established ! router(config)# access-list 110 remark **HTTP** ! router(config)# access-list 110 permit tcp any eq 80 12x.34.56.0 0.0.0.255 established ! router(config)# access-list 110 remark **IMAP** ! router(config)# access-list 110 permit tcp any eq 143 12x.34.56.0 0.0.0.255 established ! router(config)# access-list 110 remark **HTTPS** ! router(config)# access-list 110 permit tcp any eq 443 12x.34.56.0 0.0.0.255 established ! router(config)# access-list 110 remark **HP printers* ! router(config)# access-list 110 permit udp any eq 69 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp any eq 161 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp any eq 162 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp any range 9100:9102 12x.34.56.0 0.0.0.255 ! router(config)# access-list 110 remark **HP web admin* ! router(config)# access-list 110 permit tcp any eq 8000 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp any eq 8000 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp any eq 8443 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp any eq 8443 12x.34.56.0 0.0.0.255 ! router(config)# access-list 110 remark **These two sections allow NetBIOS only from router(config)# access-list 110 remark the two servers "Humpty" and "Dumpty" router(config)# access-list 110 remark to any pc on the 12x.34.56.0 subnet** ! router(config)# access-list 110 permit udp host 12x.34.50.80 eq 137 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.80 eq 137 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp host 12x.34.50.80 eq 138 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.80 eq 138 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp host 12x.34.50.80 eq 139 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.80 eq 139 12x.34.56.0 0.0.0.255 ! router(config)# access-list 110 permit udp host 12x.34.50.85 eq 137 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.85 eq 137 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp host 12x.34.50.85 eq 138 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.85 eq 138 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit udp host 12x.34.50.85 eq 139 12x.34.56.0 0.0.0.255 router(config)# access-list 110 permit tcp host 12x.34.50.85 eq 139 12x.34.56.0 0.0.0.255 ! ! router(config)# access-list 110 remark **This section allows specific ICMP packets** ! router(config)# access-list 110 remark **Allow Echo Reply packets - this could be dangerous, router(config)# access-list 110 remark as we can`t do any kind of stateful filtering on router(config)# access-list 110 remark them to link them to outgoing Echo request packets** ! router(config)# access-list 110 permit icmp any 12x.34.56.0 0.0.0.255 echo-reply ! ! ! ! That`s the end of the list for incoming packets, now we filter ! ! outgoing packets. ! ! router(config)# ! Remove the previous version of the access list ! router(config)# no access-list 120 ! ! router(config)# access-list 120 remark **This list is for outgoing packets** ! router(config)# access-list 120 remark **This section allows outgoing packets with router(config)# access-list 120 remark specific port numbers.** ! router(config)# access-list 120 remark **Because the source address is specified for router(config)# access-list 120 remark every entry, packets with spoofed ip addresses router(config)# access-list 120 remark outside the secure subnet address range will router(config)# access-list 120 remark be blocked.** ! ! router(config)# access-list 120 remark **Telnet** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 23 ! router(config)# access-list 120 remark **DNS** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 53 ! router(config)# access-list 120 remark **HTTP** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 80 ! router(config)# access-list 120 remark **IMAP** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 143 ! router(config)# access-list 120 remark **HTTPS** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 443 ! router(config)# access-list 120 remark **HP printers** ! router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 any eq 69 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 any eq 161 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 any eq 162 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any range 9100:9102 ! router(config)# access-list 120 remark **HP web admin** ! router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 8000 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 any eq 8000 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 any eq 8443 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 any eq 8443 ! ! router(config)# access-list 120 remark **These two sections allow NetBIOS only to router(config)# access-list 120 remark the two servers "Humpty" and "Dumpty" router(config)# access-list 120 remark from any pc on the 12x.34.56.0 subnet** ! router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 137 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 137 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 138 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 138 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 139 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.80 eq 139 ! router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 137 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 137 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 138 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 138 router(config)# access-list 120 permit udp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 139 router(config)# access-list 120 permit tcp 12x.34.56.0 0.0.0.255 host 12x.34.50.85 eq 139 ! router(config)# access-list 120 remark **This section allows specific ICMP packets** ! router(config)# access-list 120 remark **Allow Echo request packets** ! router(config)# access-list 120 permit icmp 12x.34.56.0 0.0.0.255 any echo ! ! ! ! router(config)# ! Configure the two interfaces, and associate the router(config)# ! access lists with them ! router(config)# interface ethernet 0 router(config-if)# ip address 12x.34.0.35 255.255.255.0 router(config-if)# ip access-group 110 in router(config-if)# no shutdown router(config-if)# exit ! router(config)# interface ethernet 1 router(config-if)# ip address 12x.34.56.1 255.255.255.0 router(config-if)# ip access-group 120 in router(config-if)# no shutdown router(config-if)# exit ! router(config)# exit router# disable router>
© 2005 Ron Turner
Return to the Cisco index page